Jim Holcomb, an Associate Security Consultant at Evolve Security, breaks down Mr. Robot's (surprisingly accurate!) portrayal of hacking in this three part series for the 1871 blog. Be warned, there's spoilers, and some crazy surprising information about real-life cybersecurity in here.
Guest Author: Jim Holcomb, Evolve Security Academy
With the season 3 premiere of Mr. Robot on the horizon, I’ve found myself prepping by rewatching some of my favorite episodes in seaeson two. In doing so, I thought it would be interesting to dive into what is happening during some of the more technical scenes. In this series, we’ll explain the technology and fundamental security concepts behind some of our favorite Mr. Robot scenes.
* Minor Spoiler Alert (duh) *
First, what is Mr. Robot and why is it awesome?
Mr. Robot is a series that follows a reclusive hacker and penetration tester named Elliot Alderson as he leads an anonymous collective known as “fsociety” in their goal to destroy a corporate banking conglomerate colloquially referred to as Evil Corp. What makes the show amazing is that it actually portrays hacking and the system exploitation in a (mostly) realistic manner. This means we actually see the characters interact with terminal prompts, execute system commands, code exploits, and discuss real vulnerabilities affecting anything from a simple website to a building’s HVAC (Air Conditioning and Heating) system.
Hollywood is infamous for playing fast and loose in their depiction of hacking which often results in absurd scenes that are so far detached from reality, it’s like watching an environmental scientist blame Poseidon for global warming. Mr Robot’s realistic approach to Information Security offers a refreshing departure from these often comical depictions.
In season 2, Elliot is out of action as he takes some time to address some mental health issues, and viewers have to wait what I considered to be a very long time before seeing Elliot get back on his feet and back in a terminal. However, once he does, it is well worth the wait. First, let’s provide some context.
In episode 5, the members of fsociety believe that the FBI is close on their tail. For this reason, Darlene, the current leader of fsociety, reaches out to Elliot requesting he provide fsociety with an exploit that will allow them to infiltrate the FBI’s network and steal the data they have related to their case against fsociety.
However, first Elliot needs to find a computer he can use to program the exploit and deliver it to Darlene. Under the guise of helping out Ray, a dark market operator and self-described “positive outlook kind of guy”, solve an issue with his website, Elliot secretly uses Ray’s computer to log into a terminal and craft an exploit targeting the FBI’s infrastructure. But what exactly is Elliot’s plan?
Finding The Target
Like any good hacker, Eliot starts by enumerating his targets. Before any system can be exploited, a hacker needs to know what sort of system or network they will be attacking. He finds a Business Insider article detailing how the FBI is transitioning their employees from Blackberry to Android.
Android and the hardware it runs on come in all shapes and sizes. Unfortunately, Android phones are notoriously difficult to keep updated due to the disconnect between Google, the primary company that distributes the Android operating system, the manufacturers that make the phone, and the telecom companies. When a device’s operating system falls behind the latest version, it becomes vulnerable to numerous publicly available exploits, and Elliot intends to take full advantage of this common scenario. And now that Elliot knows what type of system he will target, he needs to know what vulnerabilities are associated with that system.
The Vulnerability
So what’s the actual vulnerability Elliot chooses to go after? Well, while Elliot certainly may be capable of finding and exploiting his own “0days”, or unknown vulnerabilities, the actual and very real vulnerability he targets was publicly disclosed on November 12th, 2014. This will be Elliot’s way in.
But first, let’s go over the vulnerability itself. When writing the exploit, we see the phrase ‘Knox Browser RCE’ in Elliot’s code. Given this hint, we can assume that the vulnerability Elliot seeks to exploit is most likely a bug discovered by QuarksLab (view here) which involves tricking a Samsung Android phone, which ships with an application called “UniversalMDMClient” by default, into installing a malicious Android application (apk file).
So how do you actually get the exploit, which in this case is a malicious Android app, on the phone? While there are many ways to deliver the exploit, the simplest approach is to trick the user into clicking on a URL that both starts with ‘smdm://’ and points to a malicious server that you own. When clicked, the UniversalMDMClient app opens the link and attempts to parse the URL. In doing so, it will ask the URL’s server (the hacker’s server!) if the phone is running the latest available version of the UniversalMDMClient application. If the attacker controls the “smdm://” url and tricks the application into thinking a newer version is available by sending a response with a higher version number than what is installed, the application will then download and install the Android application’s apk file from that URL!
The Code
One thing that will pop out to anyone familiar with common security tools while watching Elliot work his magic is that he’s actually using a very familiar pentesting tool called the Metasploit Framework. Metasploit is an open source community driven pentesting platform written in the Ruby programming language. You can think of Metasploit as a box of Legos. Metasploit provides some pre-written code, and the hacker uses the prewritten code as building blocks as they construct the exploit. So while you see Elliot write phrases such as “register_options,” “send_response,” or “on_request_uri,”, these functions actually come from Metasploit whereas other code blocks such as “apk_bytes” provide custom functionality that Elliott has written himself.
The Payload
In his Metasploit code, Elliot sets up a malicious server. But a server needs to serve something. While he could serve some code that subscribes his victim to daily cat facts, he has something else in mind. As we can see from the video, Elliott is using the default “reverse_tcp” payload for Android. A payload typically describes what code is actually delivered to the target. In this case, it will be some sort of apk file (Android application).
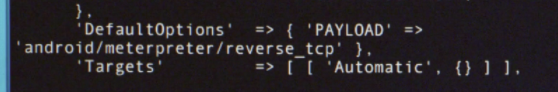
This means, that when the malicious Android application runs on the victim’s phone, the payload will provide Elliot with a remote shell to which Elliot will be able to login and perform typical system commands on the actual phone itself. While it is possible that Elliot constructs a more intricate payload off-screen, a reverse_tcp is a sensible choice if Elliot has little information about where the data he is looking for is located as it would allow him to pivot throughout the phone and investigate the next best course of action. Again, we see how useful Metasploit can be as Elliot didn’t have to actually write the payload. He just had to tell Metasploit to use the predefined payload by inserting ‘android/meterpreter/reveerse_tcp’ into his code.
The Delivery
The most interesting aspect of Elliot’s approach is how he plans to fool the FBI into visiting his server and trick them into installing his malicious android application. In passing, Elliot mentions that he will implement a “femtocell delivery system”. Sounds cool, but what is femtocell? A femtocell is a small cellular station that, among other things, essentially provides a way to funnel cellular traffic through a broadband connection. When a cell-phone searches for a tower to connect to, it will always attempt to connect to the closest one. Therefore, if you deploy a femtocell station, nearby users will automatically connect to it allowing the femtocell operator to intercept, inspect and possibly modify cellular traffic. Later in the series, Angela, a colleague and fsociety associate, will have to install on premises at Evil Corp’s Headquarters so that the FBI agents in the building with Android phones will connect to Elliott’s malicious femtocell network.
And with the Femtocell setup, all fsociety has to do is just wait for the FBI’s in Samsung devices to start connecting to it and inject a URL redirection to their malicious server. I guess you could say it’s not exactly Fort Knox.
Fsociety
The episode demonstrates how Elliott was able to use real commonly available penetration tools to target a real publicly known vulnerability in Samsung phones. Best of all, we were able to see how Elliott actually went about doing it in an actual terminal.
However, Mr Robot isn’t just meant for those in the infosec community. While it has an amazing plot, beautiful directing and a diverse cast of interesting characters, it also provides the public with some insight into how hacking actually works, and, unfortunately, how easy it can be for malicious actors to compromise the privacy of unsuspecting individuals and companies.
So what is there to do to defend against those who see any computer, phone and network as a potential target? The best defense any denizen of the internet can implement is to keep your devices up to update. Seriously. Please. Turn on auto-update. We saw how Elliott was exploiting a publicly known vulnerability that had already been patched by Samsung.
What we didn’t see (or what the show didn’t want us to know), was that Elliot didn’t write the exploit in this scene. It is a real exploit (view here). Running a Metasploit exploit is trivial to do, and anyone who spends thirty minutes reading a blog post online could perform it.
Most hackers are lazy. They go after the low hanging fruit. Don’t be a low hanging fruit. Keep your systems up to date. It’s not fancy, but it’s important.
Conclusion
I hope you enjoyed this brief breakdown explaining one of my favorite scenes from season 2. I thoroughly enjoy Mr. Robot and look forward to writing more technical breakdowns about the, tools, vulnerabilities and exploits demonstrated in the show.
Jim Holcomb is an Associate Security Consultant at Evolve Security. When he isn't colluding with our reptilian overlords, Jim enjoys developing applications and pentesting tools with Python. Questions? Email info@evolvesecurity.io.


